Strategy
"Warfare is based upon deception."
-Sun Tzu
"When able to attack, we must seem unable; when using our forces, we must seem inactive; when we are near, we must make the enemy believe we are far away; when far away, we must make him believe we are near."
-Sun Tzu
"Hold out baits and entice the enemy. Feign disorder, and crush him."
-Sun Tzu
"So in war, the way is to avoid what is strong and strike what is weak."
-Sun Tzu
"If my enemy doesn't know where I am going to attack he is forced to prepare everywhere. Forced to prepare everywhere he is strong nowhere."
-Sun Tzu
"Turn the imperialist war into a civil war"
-Lenin
"A prudent man... must behave like those archers who, if they are
skillful, when the target seems too distant, know the capabilities of
their bow and aim a good deal higher than their objective, not in order
to shoot so high but so that by aiming high they can reach the target."
-Niccolo Machiavelli
The 36 Stratagems of Ancient China
1. Fool the Emperor to Cross the Sea
2. Besiege Wei to Rescue Zhao
3. Kill With a Borrowed Sword
4. Await the Exhausted Enemy At Your Ease
5. Loot a Burning Building
6. Make a Noise in the East, and Strike in the West
7. Create Something From Nothing
8. Openly Repair the Walkway, Secretly March to Chanan
9. Observe the Fire on the Opposite Shore
10. Hide the Dagger Behind a Smile
11. Let the Plum Tree Wither in Place of the Peach
12. Seize the Opportunity to Lead the Sheep Away
13. Beat the Grass to Startle the Snake
14. Borrow a Corpse to Raise the Spirit
15. Lure the Tiger Down the Mountain
16. To Catch Something, First Let It Go
17. Toss Out a Brick to Attract Jade
18. To Catch the Bandit First Capture Their Leader
19. Steal Fire Wood From Under the Pot
20. Trouble the Water to Catch the Fish
21. Shed Your Skin Like the Golden Cicada
22. Shut the Door to Catch a Thief
23. Befriend a Distant Enemy to Attack a Nearby Enemy
24. Borrow the Road to Conquer Guo
25. Replace the Beams With Rotten Timbers
26. Point At the Mulberry Tree, But Curse the Locust Tree
27. Feign Madness, But Keep Your Balance
28. Lure Your Enemy Onto the Roof, Then Take the Ladder
29. Deck the Dead Tree With Silk Blossoms
30. Exchange the Role of Guest for that of Host
31. The Strategy of Beautiful Women
32. The Strategy of Open Gates
33. The Strategy of Sowing Discord
34. The Strategy of Injuring Yourself
35. The Strategy of Combining Tactics
36. If All Else Fails...Retreat
Blitzkrieg ("Lightning War")
Relies upon rapid speed and force to quickly break through enemy lines. Uses combined arms of aircraft, vehicles, and infantry.
The rapid military movements and sweeps into various cities and strategic positions mimic the arcs and branches of a lightning strike.
Flanking Maneuver (Single Envelopment)
Pincer Movement (Double Envelopment)
Encirclement
Breakout
Breaking out of enemy encirclement
Guerrilla forces break down into smaller groups and sneak past enemy lines. Guerrilla forces reassemble at predesignated location.
Siege
Blockade
Land Blockade
Example:
Blockade of the Nepalese capital Kathmandu by the Communist party of Nepal (CPN) during the Civil War in Nepal. Highways and roads leading to the capital were frequently blocked by CPN supporters.
Sea Blockade
Guerrilla Blitzkrieg
Popular Revolt or Civil Uprising
At this stage the guerrillas should outnumber the enemy and should have the support of the masses. The entire population can then be mobilized to sweep the enemy out of the nation. Success depends on the support of the majority of the population. Offensive plans are made in advance. More conventional stage of warfare.
Speed and mobility are essential. Must have the ability to destroy a target and quickly move on to the next target.
Destroy everything belonging to the enemy that you cannot use.
All enemy businesses, factories, etc., should be destroyed or taken over.
Stay close to the enemy and engage in close combat.
Pockets of resistance should be bypassed by the main force and dealt with later by mop up forces that surround the enemy pocket and destroy them.
Possible military commanders and potential leaders and organizers among the enemy should be targeted for assassination.
Enemy vehicles are captured or commandeered and civilian vehicles are used for transportation.
Take fuel from gas stations or parked vehicles and keep moving.
Block or ambush enemy reinforcements
Historical Examples:
FSLN forces capture Managua, the capital of Nicaragua in July of 1979
The 1968 Viet Cong Tet Offensive was actually a failed attempt at a popular uprising.
The French resistance uprising against German forces in Paris as the Allied forces advanced towards the city.
The Polish resistance uprising against German forces in Warsaw in 1944.
Anarchopoly
During a popular uprising rioters can plan to raid and/or destroy certain buildings in advance of riots. Quickly move from building to building, street to street, taking certain items of use. Facilities owned by the enemy are burned down. Weapons and equipment taken. Anything taken from friendly businesses is "borrowed" or perhaps even purchased. Businesses to raid and items to be taken are planned in advance. Scouts can secretly make note of current inventory days or weeks in advance. Scouts take note of positions of cameras as well. Rioters can wear masks regardless. Cameras can be smashed with sticks, bats, etc. or painted over with spray paint during rioting or even before rioting or uprising.
Rapidly take over or destroy certain businesses and move on to the next one. Take out what is needed for the movement and destroy the rest.

Quick strike guerrilla offensive such as an FLNC style "nuit bleu" or "Blue Night". This style of attack is more of an overnight Blitzkrieg. Multiple sites are attacked overnight. Series of Hit and Run attacks.
Preemptive Strike (Conventional)
A surprise attack to prevent the enemy from launching a surprise attack on oneself or simply to attack the enemy before he can attack you. This is good to do during the enemy buildup of forces.
Preemptive Strike (Guerrilla)
Sympathizers in one nation attack an enemy during his buildup to invade another nation. Fire rockets, mortars, etc. at his staging areas and encampments. Use guerrilla tactics. If and when the enemy invades, the guerrillas continue to attack the enemy in the rear.
Examples:
08 OCT 2002- 2 U.S. marines are shot in Kuwait during a military exercise in preparation for the invasion of Iraq. One of the two marines later dies. The two gunmen that attacked them are martyred.
21 JAN 03- 2 more americans shot in Kuwait. 1 of them dies from wounds. Both were civilian contractors working for the U.S. military. Shot sitting in their SUV at a red light.
30 MAR 03- 13 U.S. soldiers are injured by an Arab contractor driving a truck in Kuwait. The driver purposely plowed into a crowd of soldiers at a camp PX.
Counter Attack
Strategic sabotage can paralyze entire armies.
Further Reading on Strategy:
The Art of War- Sun Tzu
The Book of Five Rings- Miyamoto Musashi
The 36 Stratagems of Ancient China
Guerrilla Warfare
Low Intensity Warfare
Strategy Used in Guerrilla War
“Our Strategy is one against ten. Our tactic is ten against one.”
-Mao Tse Tung
Mao's Three Stages of Guerrilla Warfare
1. Preparation and Organization. The establishment of guerrilla base areas.
2. Sabotage and Guerrilla Warfare phase.
3. Strategic Counter-Offensive. Conventional War phase including large unit and mobile warfare. The final phase places an emphasis on a popular uprising of the masses in conjunction with the liberation forces.
Must have a clear political objective.
Lack of numbers and technology can be made up for using special tactics, better knowledge of the land, deception and determination.
Harass and tie down the enemy and destroy the enemy's forces and supplies.
Fire off isolated shots, fire crackers, wooden clappers, etc. to harass the enemy and keep the enemy on edge
Do not attack strong positions
Do not fight an uphill battle.
Do not fight if the situation of the enemy is not clear.
Do not fight hard battles. If you are not one hundred percent certain of victory, do not fight.
Constant offensive action against enemy personnel and sensitive points, but only when the tactical advantage is on the side of the guerrillas.
In order to achieve a quick decision in battle, attack a moving enemy unit, not a stationary enemy. Concentrate a large force under cover and attack a smaller enemy unit along a route the enemy is sure to take.
Multiple guerrilla groups can be formed. These separate guerrilla groups have no real connection to one another other than a similar goal or agenda. If one group or cell is destroyed or captured, it does not effect the operations of the movement as a whole.
"Lure the enemy in deep."
In order to draw the enemy into a trap, or ambush, entice the enemy with something he wants. A strategic position, a decisive battle, a secret base, a guerrilla leader, sex, food, money, a downed pilot, sleep, the chance for fame and glory, etc., all could be used to entice the enemy into advancing using the Five Needs or the Five Weaknesses.
Sources of weapons
The enemy can be the chief source of weapons for the guerrilla
Weapons can be captured during raids or stolen from enemy sources

Weapons can be taken off dead enemy soldiers
Weapons can be purchased on the underground illegal market.
Improvised weapons can be made by guerrilla forces.
Safe houses for guerrillas in urban environments after an operation.
Protracted War
Patience is required while enduring protracted wars.
"Time works for us. Time will be our best strategist." -Truong Chinh
Resistance Movement
Revolutionary War
"Peoples War"
Political Strategy
Integrate political and military efforts.
The war should be waged on all fronts; diplomatically, ideologically, economically,
and militarily.
Total mobilization of the people by propaganda, motivational and organizational measures.
Intense indoctrination of both military and civilian personnel.
Political Action Among Enemy Military Forces
Subversion
Proselytizing
Propaganda to encourage desertion, defection, and to lower enemy morale. An example of this is to contribute to enemy deserters and draft dodgers.
Counter Recruitment - The discouraging of soldiers from being recruited into government or opposition forces.
Political Action Among the Enemy's Population
A total propaganda effort to sow discontent, defeatism, dissent, and disloyalty among the enemy population. This may involve the creation and/or manipulation of front groups and sympathizers. An example of this is to work among enemy media, activist, etc.
"Turn the imperialist war into a civil war!"
When an imperialist nation launches another war, the people of that imperialist nation are to rebel against the corrupt leadership and initiate a civil war.
Further Reading on Guerrilla Warfare:
On Guerrilla Warfare- Mao Zedong
Basic Tactics- Mao Zedong
150 Questions For A Guerrilla- General Alberto Bayo
Total Resistance- Major Hans von Dach
Minimanual of the Urban Guerrilla- Carlos Marighella
Guerrilla Warfare- Ernesto Guevara
Very Low Intensity Warfare
Ninjutsu
Heiho (Hei ho)- Strategy and tactics
Few in number, ninja attempt to influence outside forces in order to get a desired result. Intricate plans are made to get the enemy to do precisely what you want him to do. Intrigue.
One of the main goals in ninja strategy and planning is to remain undetected.
A strategy using espionage, sabotage and assassination as the main means of defeating an enemy.
Espionage
Sabotage
Assassination
Ambush
Psychological Warfare
The Five Needs
Security
Sex
Wealth
Pride
Pleasure
The Five Weaknesses
Laziness
Anger
Fear
Sympathy
Vanity
The use of modern day weapons and equipment such as:
Explosives (hand grenades, plastic explosives, etc.)
Night vision goggles and scopes
Firearms and suppressed firearms
Bows and Crossbows
Combat knives
The use of traditional ninja weapons.
The use of traditional tribal weapons from the area of operations.
Improvised traditional ninja weapons.
Uniforms
Civilian clothes
Enemy military uniforms.
Enemy police uniforms.
Construction worker, repair person, businessman, etc.
Camouflage, black or dark blue uniform similar to, but not limited to, that of the ninja. In an urban environment, the actual use of this uniform will be extremely rare.
Organization and Structure
Jonin- "High Ninja"
Chunin- "Middle Ninja"
Genin- "Lower Ninja"
Reconnaissance should be done before even considering an actual operation in an area.
Check for security cameras, security personnel, views from civilians, fences, locks, sensors, dogs, etc.
Further Reading on Ninjutsu:
The Way of the Ninja: Secret techniques- Masaaki Hatsumi
The Ninja and Their Secret Fighting Art- Stephen K. Hayes
Ninjutsu: History and Tradition- Masaaki Hatsumi
Tiger Scroll of the Koga Ninja- Jay Sensei
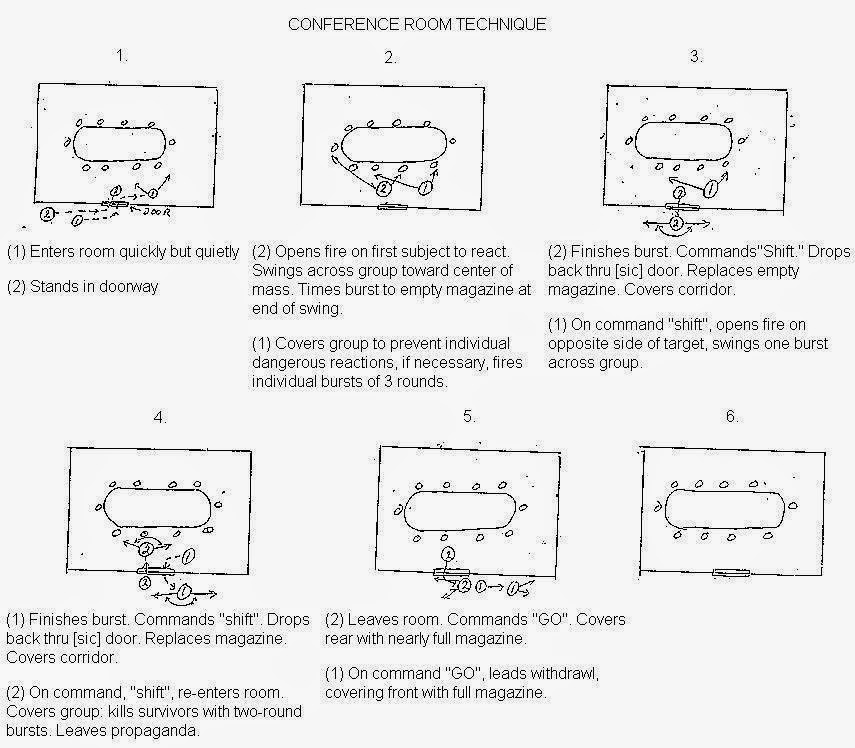
Section Omitted
Leaderless Resistance
Lone Wolf
Like minded individuals or groups with no real leadership or command structure fighting against a common enemy.